Use Red Zones to find memory access violations
When your program allocates a memory block, MemoryScape can write an additional memory buffer either before or after the block. These buffers are called Red Zones. MemoryScape watches the Red Zone for illegal read or write access.
NOTE >> Red Zone controls appear on the toolbar only on platforms that support Red Zone capabilities. See the Platform Guide for specific platform support. |
To enable Red Zones, set the debugging level to High (in the Basic Options) or select the option “Use Red Zones to find memory access violations” on the Advanced Options screen, Figure 47.
Figure 47: Advanced Red Zone Option |
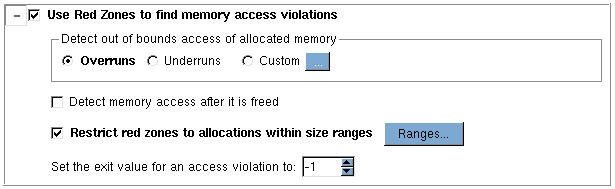 |
This dialog controls the type of error to detect and defines ranges and values for some of the detection types. In addition to detecting overruns and underruns (discussed above), you can customize Red Zone definitions, discussed in Customizing Red Zones.
Red Zones can help identify where an illegal access occurs in these cases:
• Overruns: reads or writes past the bounds of the allocated block, detected by placing a Red Zone after the block.
• Underruns: reads or writes before the bounds of the allocated block, detected by placing a Red Zone before the block.
• Read / write access after a block is deallocated.
If you select “Detect memory access after it has been freed”, you are notified when this occurs. MemoryScape retains the deallocated blocks to monitor them for both read and write access. This option will increase memory consumption in your program.
One way to limit the overhead incurred in using Red Zones is to restrict their use to blocks of specified sizes. (See Restricting Red Zones for details on using the option “Restrict Red Zones to allocations within size ranges.”) Another way is to turn Red Zones on and off during program execution using the Red Zones button  ,on the toolbar. Because of the increased memory consumption associated with Red Zones, use them with caution.
,on the toolbar. Because of the increased memory consumption associated with Red Zones, use them with caution.
 ,on the toolbar. Because of the increased memory consumption associated with Red Zones, use them with caution.
,on the toolbar. Because of the increased memory consumption associated with Red Zones, use them with caution. To know when your program exits due to an access violation, use the last option, “Set the exit value for an access violation.”
NOTE >> For a detailed description of how Red Zones work, see Red Zones Bounds Checking: dheap -red_zones. |